
North Korean hacker group orchestrated a chain attack that allowed it to monitor corporate customers' communications through the 3CX Virtual PBX platform, modify call routing or broker connections on external voice services
CLM, Latin American value-added distributor focused on information security, data protection, cloud and data center infrastructure, warns of a new type of attack, made in chain, with the aim of accessing source codes, creating processes or updating mechanisms, infecting legitimate applications to distribute malware. 3CXDesktopApp, a well-known 3CX application used for voice and video conferencing and categorized as an IP PBX platform (internet telephony and video) has been compromised in recent days as part of a chain attack called “SmoothOperator”, filed by the North Korean APT group, Labyrinth Chollima, associated with Lazarus.
The information comes from analyzes carried out by the SentinelOne, specializing in cybersecurity technologies based on artificial intelligence, ranging from prevention, detection, response and hunting to attacks, and for Picus Security, a pioneer in Breach and Attack Simulation (BAS). Both solutions are distributed by CLM.
 According to CLM CEO Francisco Camargo, chain attacks are emerging threats that target software developers and vendors. “In the case of chain attacks, the attackers trojanize an application, that is, they install a parasite, a malware, which will be distributed within the application, to thousands of customers and which create an access door (backdoor) so that other malicious software can use it to invade the system”, explains the executive.
According to CLM CEO Francisco Camargo, chain attacks are emerging threats that target software developers and vendors. “In the case of chain attacks, the attackers trojanize an application, that is, they install a parasite, a malware, which will be distributed within the application, to thousands of customers and which create an access door (backdoor) so that other malicious software can use it to invade the system”, explains the executive.
To get an idea of the extent of this attack, 3CX claims, on its website, that it has 600,000 customer companies, from various segments such as automotive, IT managed service providers (MSPs), manufacturing, etc., with 12 million users daily.
According to Picus analysis, in March 2023, the APT group inserted malicious code into the 3CXDesktopApp application code and unsuspecting users installed the contaminated versions through direct downloads or updates.
CHAIN ATTACK DETAILS
SentinelOne explains that in the case of 3CXDesktopApp, the app was trojanized, this being the first stage of a multi-stage attack chain, when ICO files attached with base64 data were extracted from Github which then led to an infostealer DLL .
“As we actively analyze the malicious installer, we see an interesting multi-stage attack chain unfolding. The 3CXDesktopApp application serves as a shellcode loader with shellcode executed from heap space. The shellcode reflexively loads a DLL, removing the “MZ” at the beginning. This DLL, in turn, is called, through an export named 'DllGetClassObject', with the following arguments:
1200 2400 “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) 3CXDesktopApp/18.11.1197 Chrome/102.0.5005.167 Electron/19.1.9 Safari/537.36”
As well as the size of this User-Agen chain”, informs the SentinelOne report.
According to Picus analysis the affected versions of 3CXDesktopApp versions are:
- 3CX DesktopApp – Electron Windows App
- versions 18.12.407 and 18.12.416
- 3CX DesktopApp – Electron Mac App
- versions 18.11.1213, 18.12.402, 18.12.407, and 18.12.416
While these versions are signed using 3CX digital certificates, users are advised not to use these versions.
In this first stage, the trojan downloaded icon files from a dedicated Github repository:
https://github[.]com/IconStorages/images
After installation, compromised versions of 3CXDesktopApp contact the attackers' control C2 servers and install information-stealing malware called ICONICSTEALER. This malware is used to steal sensitive data from compromised systems.
These ICO, image files have Base64 encoded data attached at the end, which is decoded by attackers and used to download another stage of the attack. The DLL file appears to be an unknown infostealer, intended to interact with the browser's data, likely in an attempt to allow future operations as attackers comb through the mass of infected clients.
The final stage (cad1120d91b812acafef7175f949dd1b09c6c21a) implements the infostealer functionality, including collecting information from the system and from Chrome, Edge, Brave and Firefox browsers. This includes querying browsing history and local data on Firefox-based browsers and history for Chrome-based browsers.
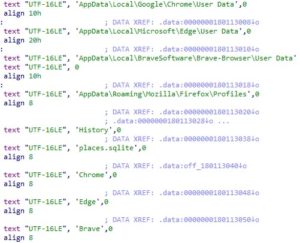
Infostealer strings used to query history and places list
The 3CX PBX client is available for Windows, macOS and Linux; there are also mobile versions for Android and iOS, as well as a Chrome extension and browser-based Progressive Web App (PWA) client version. Picus reports that both the Windows and macOS versions of 3CXDesktopApp are affected.













