SentinelOne detects the use of Geacon malware beyond Windows. The target now is the Go implementation of Apple's operating system, MacOS.
CLM, Latin American value-added distributor focused on information security, data protection, cloud and data center infrastructure, warns of Geacon malware, in attacks against devices running Apple MacOS. Widely used by Red Teams of security companies and SOCs, Cobalt, an attack simulation platform, was already being used frequently by cyberattackers against Windows platforms.
According Pedro Diógenes, CTO of CLM, in recent months, the SentinelOne, specializing in AI-based cybersecurity technologies ranging from attack prevention, detection, response and hunting, observed several Geacon payloads on VirusTotal, a free online service that analyzes files and URLs to identify malicious content detectable by antivirus and scanners on websites.
“It is likely that some of these attacks are Red Team operations, but others, according to SentinelOne's analysis, have characteristics of authentic malicious attacks. Apparently, cyberattackers use the public project and even the private forks of Geacon. In addition, the increase in Geacon samples in recent months indicates that security teams should pay attention to this tool and ensure that their networks have active protection”, warns Diogenes.
What is Geacon?
Geacon is a project that appeared four years ago on Github like the Cobalt Strike Beacon Go implementation. Despite being widespread, until recently SentinelOne had not seen its deployment against Apple targets running MacOS. Looking at the payloads on VirusTotal, it appears that what has changed is the popularity of the two forks of Geacon, created by an anonymous Chinese developer who identifies himself as “z3ratu1”.
In a post on blog popping candy, at the end of October 2022, z3ratu1 states that “one day I went shopping and saw this geacon project, so this experimental project and its development guide came up”. The first payload of Mach-O Geacon was submitted to VirusTotal not long after, on November 10 last year.
In April of this year, public projects geacon_plus and private ones (possibly for sale) geacon_pro, developed by z3ratu1, “earned almost 1k stars” and were included in the 404 Starlink project, a public repository of open source Red Teams and penetration tools maintained by the Zhizhi Chuangyu Lab. In the same month, two different Geacon payloads were sent to VirusTotal that caught the attention of SentinelOne. One in particular bore the earmarks of a genuinely malicious campaign.
How to protect yourself from Geacon payloads
The SentinelOne platform identifies Geacon payloads as malicious and eliminates them on write (in protection mode) or on execution (in detection mode).
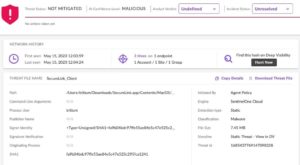
Technical breakdown of two recent attacks by Geacon
Resume_20230320.app by Xu Yiqing
Xu Yiqing's Resume_20230320.app was submitted to VirusTotal on April 5th. This applet uses a compiled run-only AppleScript to trigger a remote C2 server and download a Geacon payload.
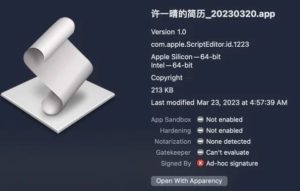
The application was co-designed ad hoc and compiled for Apple Silicon and Intel architectures. Analysis of the run-only script shows that it contains logic to determine the current architecture and download a Geacon payload created specifically for the target device.
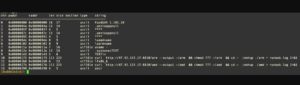
Geacon Dropper C2 Strings
The unsigned Geacon payload is downloaded from an IP address in China. Before starting their signaling activity, the user is presented with a two-page “bait” document embedded in the Geacon binary. A PDF opens displaying a CV of a person named “Xu Yiqing”.
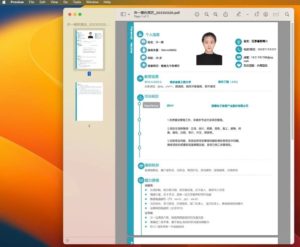
PDF "bait" of Geacon
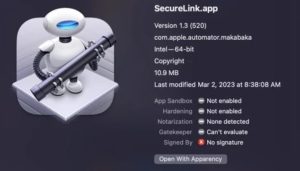
Trojan payload disguised as SecureLink
A second Geacon payload appeared on VirusTotal on April 11th. In this case, the payload, fa9b04bdc97ffe55ae84e5c47e525c295fca1241, is incorporating a trojan disguised as SecureLink, an enterprise application for secure remote support.
Diógenes explains that the trojan or Trojan horse is a simple, unsigned application, created from an Automator workflow, an app developed by Apple for OS X, instead of a Script Editor applet, and has the com.apple.automator.makabaka package identifier. This binary code targets only Intel devices.
Prevention is better than cure: BAS in cybersecurity
In order not to take risks, the CLM executive clarifies that there are pioneering Breach and Attack Simulation (BAS) solutions in the world that help companies to improve their cyber resilience.
“The simulation reverses the dynamics of zero day in favor of the organization, zero trust, allowing them to be proactive in prevention. Picus Complete Security Control Validation, for example, shows how a cybercriminal could steal confidential data from a company and monitor, in real time and on an ongoing basis, that systems are configured correctly, allowing for corrections and enhancements. In addition to analyzing the configuration of security devices and other network assets”, he concludes.
Technical details of payloads in Geacon
Resume_20230320.app by Xu Yiqing
Below are the details of the Intel x86 payload, simply called amd (bef71ef5a454ce8b4f0cf9edab45293040fc3377). The embedded PDF is called from the main.makewordfile function.
The compiled Geacon binary code has a multitude of functions for tasks such as network communications, encryption, decryption, downloading other payloads, and data exfiltration.
Main functions of a Geacon payload
The C2 server, in both the first and second stages, is a Chinese IP address 47.92.123.17, which is associated with other malicious samples targeting Windows machines.
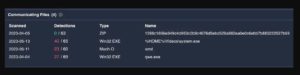
Files communicating with IP 47.92.123.17 (source: VirusTotal)
The source indicates that this sample was compiled from the free geacon_plus source code.
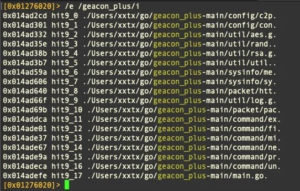
SecureLink.app and SecureLink_Client
Payload, a trojan disguised as SecureLink
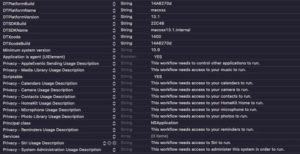
Info.plist reveals that the app was built on a macOS Ventura 13.1 device and targets macOS versions from OS X 10.9 Mavericks onwards. It also requires the user to grant access to the device's camera, microphone, and administrator privileges, as well as data such as contacts, photos, and reminders that would otherwise be protected by the device. TCC.
The application's main executable is a Geacon payload created from the geacon_pro private project.
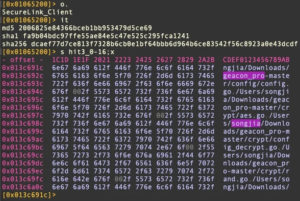
The user path to the geacon_pro source remains hard-coded in the binary
In this sample, C2 is a Japanese IP address, 13.230.229.15, widely recognized as a Cobalt Strike server on VirusTotal.
SentinelOne was unable to identify whether this sample is operationally connected to the Xu Yiqing resume.app. But this isn't the first time you've seen a Trojan disguised as SecureLink with an integrated open-source attack framework: a sliver implant was being distributed as a fake SecureLink app in September 2022.
“We can conclude that corporate Macs are now being targeted by a variety of threat actors,” Diogenes points out.
Geacon IoCs
For companies not protected by SentinelOne or Picus Security, CLM reproduces below the list of Geacon Indicators of Compromise (IoCs), made by experts at SentinelOne. “Our objective is to help detect and search for cyber threats”, concludes Pedro Diogenes.
Geacon SHA1s
6831d9d76ca6d94c6f1d426c1f4de66230f46c4a
752ac32f305822b7e8e67b74563b3f3b09936f89
bef71ef5a454ce8b4f0cf9edab45293040fc3377
c5c1598882b661ab3c2c8dc5d254fa869dadfd2a
e7ff9e82e207a95d16916f99902008c7e13c049d
fa9b04bdc97ffe55ae84e5c47e525c295fca1241
Geacon on observed C2s servers
47.92.123.17
13.230.229.15
Packet Identifiers
com.apple.ScriptEditor.id.1223
com.apple.automator.makabaka
Suspicious File Paths
~/runoob.log













