CLM and NSFOCUS analyze the main occurrences, types, sizes and new attacks, which were blocked by the cloud-based DDoS Protection System (DPS)
THE CLM, a Latin American value-added distributor focused on information security, data protection, cloud and data center infrastructure, analyzes the report on DDoS attacks in terms of their distribution by bitrate, types, traffic trends and the ones that emerged in 2022 by NSFOCUS, a global provider of intelligent hybrid security solutions.
It is important to observe, evaluates CLM's international and product vice-president, Gabriel Camargo, that the study was carried out based on attacks against cloud infrastructures of ISP/IDC/Hosting service providers, companies, governments, the education sector and internet content providers, which happened in 2022, and were mitigated by the NSFOCUS cybersecurity operations center, with its NSFOCUS cloud-based DDoS Protection System (DPS) solution.
 Report brings real scenario
Report brings real scenario
“Therefore, we are talking about a real scenario, which portrays the fight between hackers versus defense systems that effectively block DDoS attacks”, comments the CLM executive, which distributes NSFOCUS solutions.
1. The DDoS attacks traffic trend, in 2022, remained relatively stable throughout the year, with volumetric incursions of more than 150 gigabits per second (Gbps), recorded every month.
2. Of the attacks, which took place in 2022, 68.24% were less than 5 Gbps and 2,18% were greater than 100 Gbps.
3. In the chart below, NSFOCUS has identified attack sizes larger than 1Gbps distributed month by month and how much each size represents within a given month.
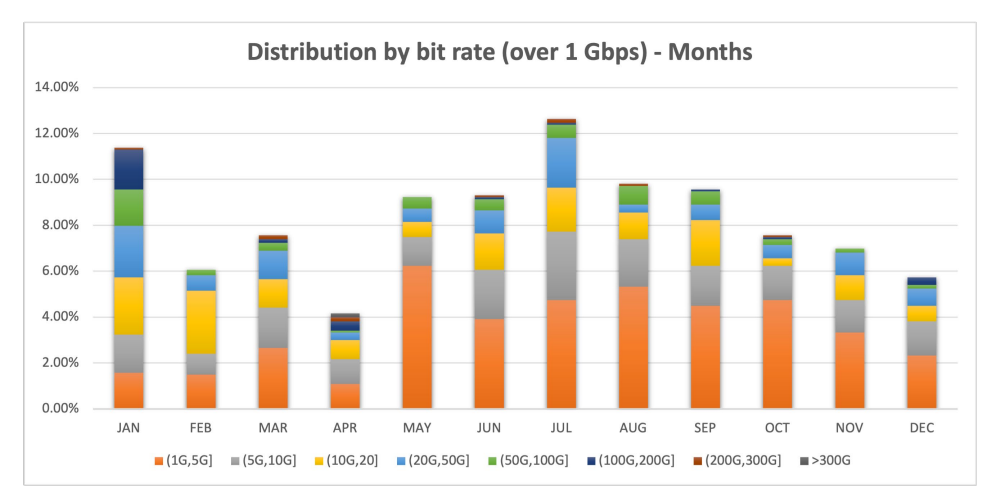
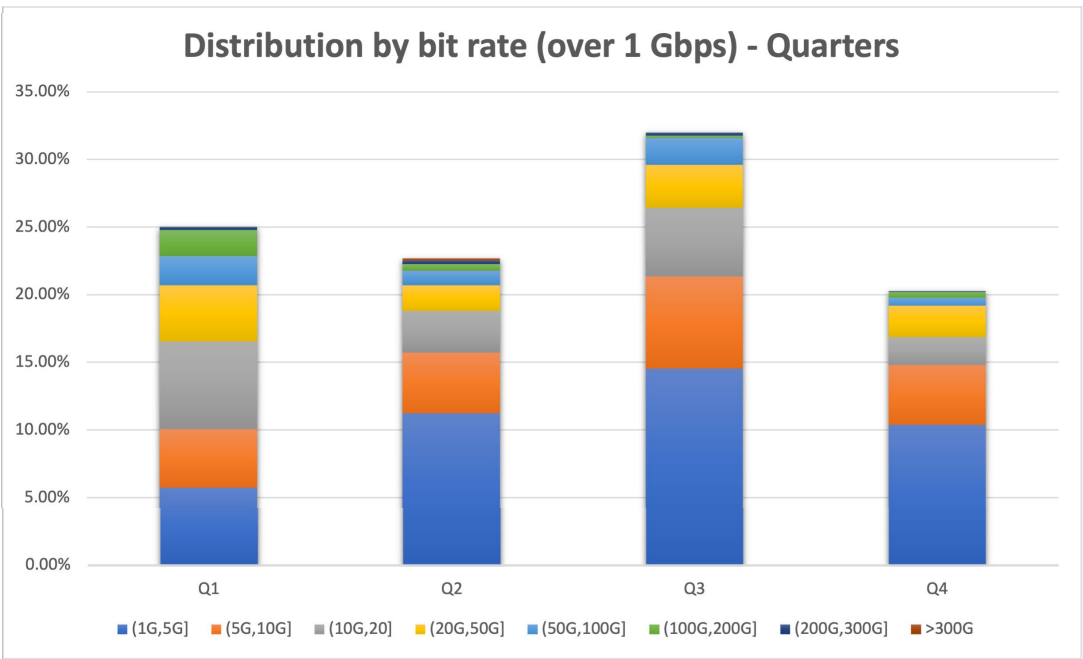
4. NSFOCUS noted that the third quarter of 2022 saw record volumes, accounting for 30% of the total attacks greater than 1 Gbps for the entire year.
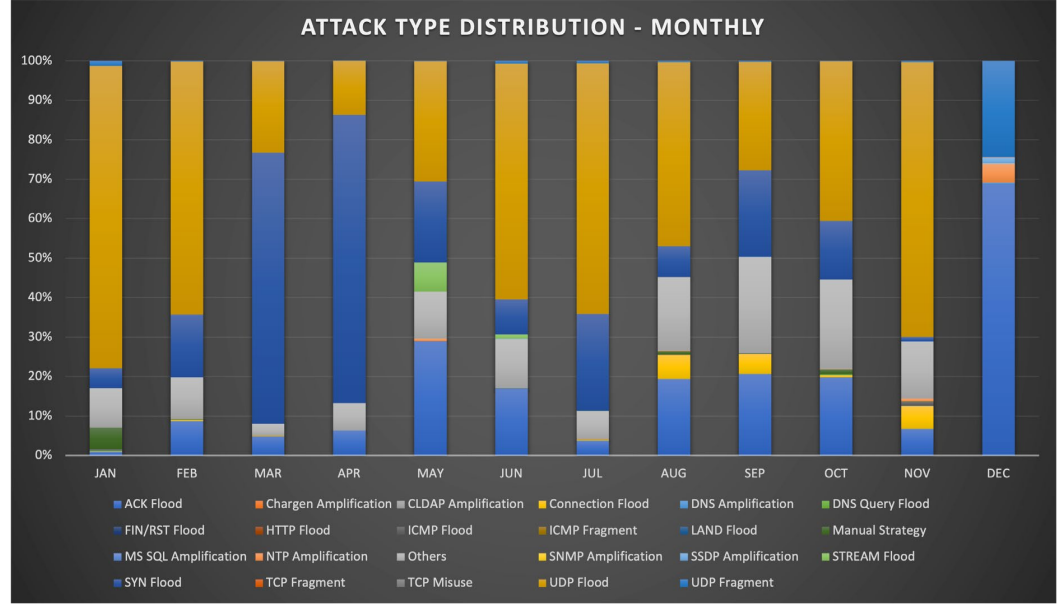
5. When analyzing the types of attack, month-to-month, the company noted that the UDP Flood was still prevalent and was highlighted in January 2022. The ACK Flood took second place.
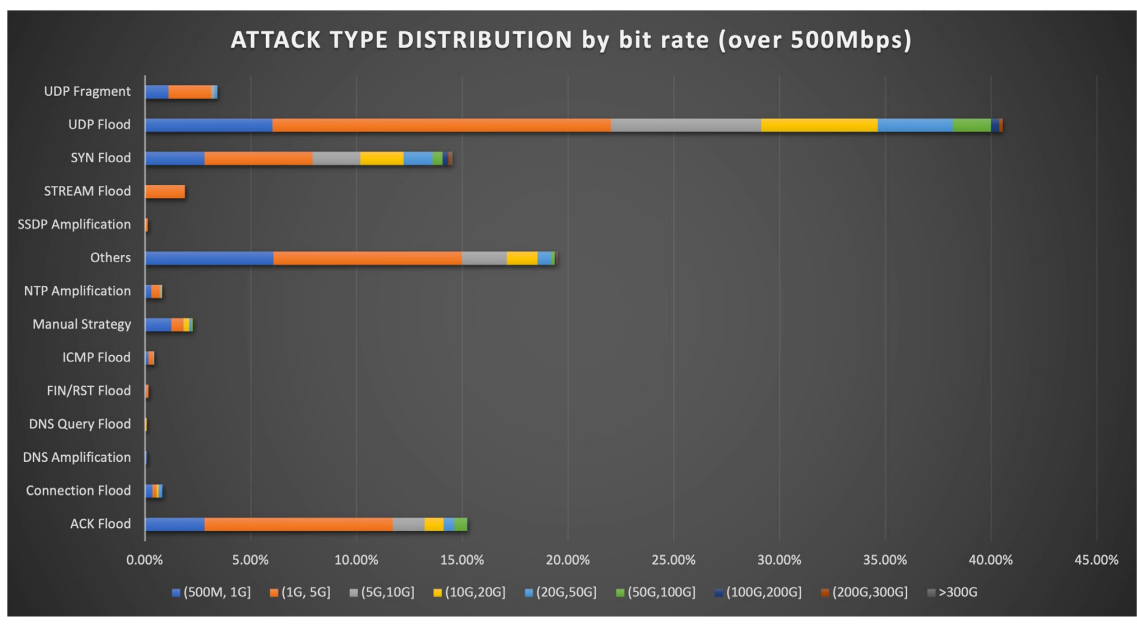
6. NSFOCUS also identified types of DDoS attacks above 500Mbps
7. The three peaks, in terms of size, took place in April 2022, when NSFOCUS mitigated a volumetric DDoS attack at a peak of 309.4 Gbps, including 302.2 Gbps SYN Flood, with cleanup efficiency reaching 99.87%.
Another volumetric DDoS attack mitigated by NSFOCUS peaked at 303.7 Gbps, including 302.9 Gbps SYN Flood, with a cleanup efficiency of 99.73%.
And the third volumetric attack containing 271.6 Gbps UDP Flood peaked at 273.9 Gbps, being mitigated by NSFOCUS, with a cleaning efficiency of 99.19%.
8. New types of attacks in 2022
Reflection Amplification Attack based on CVE-2022-26143 9.1.1
NSFOCUS captured a customer's UDP Flood traffic and found the destination port to be 10074, related to recently discovered vulnerability exploits. In this incident, the attacker using TP-240 reflection/amplification could launch a high-impact DDoS attack using a single packet. Examination of the tp240dvr binary reveals that, due to its design, it theoretically allows the attacker to cause the service to issue 2,147,483,647 responses to a single malicious command. Each response generates two packets on the network, leading to about 4,294,967,294 amplified attack packets that are directed at the victim.
Mitigation of the attack
NSFOCUS throttled UDP traffic to the protection group in which the client's IP address was contained. And it captured some packets when UDP Flood escaped the protection algorithm, finding that UDP had HTTP headers information in data.
Camargo explains that these packages are frequently used for communications between IoT devices. “Attackers can use reflection to make some IoT devices on the public network become reflection sources for DDoS attacks,” he points out.
To mitigate NSFOCUS attacks performed pattern matching on UDP traffic and dropped packets starting with HTTP/1.1 in the data field. Then he worked with the customer to block traffic on the non-business port.
All IP addresses on the same customer network prefix were attacked with 100 Mbps UDP at the same time, affecting their bandwidth. The attacker used a large number of bot devices on public network to send a small number of UDP data packets to multiple IP addresses on the destination network segment. In this way, it was very easy to achieve the attacker's goal of occupying the target bandwidth, as the small number of packets makes it difficult to trigger the protection threshold.
As a short-term measure, you should put the victim's IP segment in a separate protection group and use a lower UDP limit to limit its speed. And the long-term recommendation is to use NSFOCUS Threat Intelligence (NTI) to identify and block IP addresses on the public network where carpet bombing attacks exist.
The study is available at link. It is worth remembering that all data comes from the Active Defense Business Operations System (ADBOS) of NSFOCUS.













