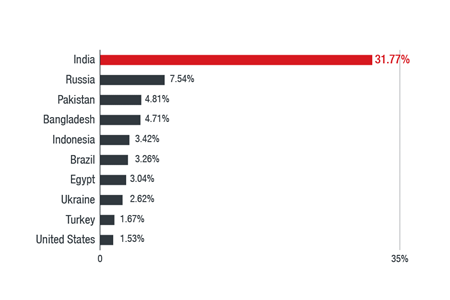
Part of what makes this case interesting is how widely your applications have been distributed. Trend Micro's back-end monitoring and in-depth research shows that it is distributed across different countries and that the affected users came from a total of 196 different countries. Brazilians were the sixth most affected worldwide:
One of the applications initially investigated was the game called Flappy Birr Dog. Other applications included FlashLight, HZPermis Pro Arabe, Win7imulator, Win7Launcher and Flappy Bird. Google has already removed all of these apps from Google Play.
.png)
Information theft
"MobSTSPY" is able to steal information such as the user's location, SMS conversations, call logs and clipboard items. Once the malicious application is launched, the malware will first check the device's network availability. It then reads and parses an XML configuration file from your C&C server.
The malware will then collect certain information from the device, such as the language used, the registered country, the package name, the device manufacturer, etc. Depending on the command received by the malware, it can steal SMS conversations, contact lists, files and call logs. The malware is even capable of stealing and uploading files found on the device.
Felippe Batista, cloud information security specialist at Trend Micro, warns users to be cautious when downloading, no matter how much the app is within the official operating system stores. “The popularity of applications serves as an incentive for cybercriminals to continue to develop malicious software to steal information or carry out other types of attacks. In addition, users can install a comprehensive cybersecurity solution to defend their mobile devices against mobile malware. ”
Phishing capabilities
In addition to its information-stealing capabilities, malware can also collect additional credentials through a phishing attack. It is capable of displaying fake Facebook and Google pop-ups for phishing the user's account details. If the user enters their credentials, the fake pop-up will only report that the login was not successful. At that point, the malware would have already stolen the user's credentials.
This case demonstrates that, despite the prevalence and usefulness of applications, users must remain cautious when downloading them to their devices.












