Threats blocked in the first half of 2023 already correspond to 59% of the total attacks registered last year
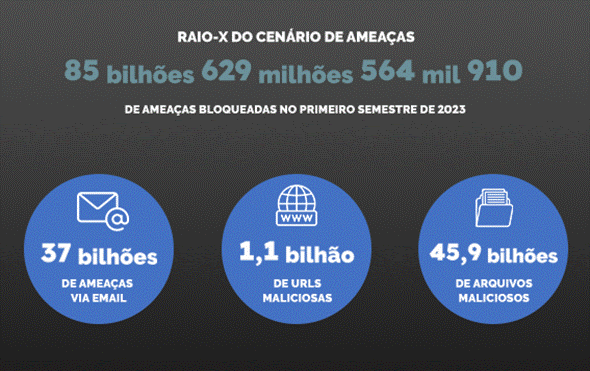
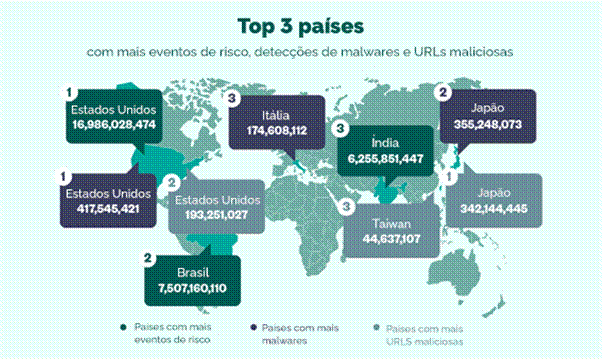
Report of Trend Micro, a world leader in cybersecurity solutions, reveals a total of 85.6 billion threats blocked in the first half of this year, almost 59% of the total recorded in 2022, which was 146 billion. Data from the Attack Surface Risk Management (ASRM) tool confirms the growing trend in cybercrime activities and shows that United States, Brazil and India were priority targets in these first six months of the year.
“Since 2013, Brazil has been the main target in Latin America and one of the countries most targeted by digital criminals around the world. To increase the level of protection, it is essential that organizations and companies adopt multi-layered security solutions, to increase visibility and detection of suspicious behavior, and to have a quick response in the case of intrusions”, highlights César Cândido, general director of Trend Micro Brazil.
The report shows that the main vector of action of criminals this semester were malicious files, with a total of 45.9 billion attacks, corresponding to 53.6% of the total number of blocks carried out by Trend Micro in the period. A industry was the preferred target of cybercrime in these first six months of the year, with more than 10 billion attacks, followed by the healthcare (9.7 billion), technology (9.5 billion), retail (7.8 billion) and government (6.4 billion) sectors.

The attacks by email were also widely used by cybercriminals, with more than 37 billion (43%) malicious attacks in the semester. The United States was the country most attacked by this type of strategy, followed by China, the Netherlands, France and Russia.
ransomware
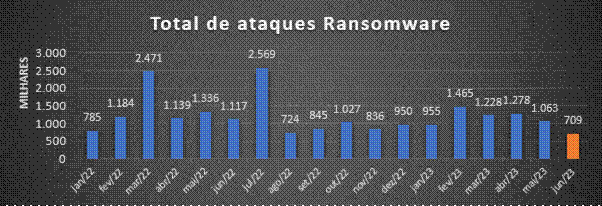
Ransomware attacks continue the downward trend observed in recent years, totaling almost 6 million and 700 thousand cases in the first six months of 2023, around 1 million and 300 thousand fewer cases than in the same period last year. Experts attribute this reduction in numbers to the fact that criminals act increasingly with focus and direction, using innovations creatively to increase efficiency, productivity and profitability.
The segments most affected by ransomware in the first half of 2023 were banking, retail and transportation. Turkey, the United States and Japan were the countries that suffered the most from this type of attack. The five most active ransomware families in the period are: Locky, Gorf, Cerber, BlackBasta and LockBit.
Trend Micro researchers explain that criminals have expanded their network through new tools and partnerships, taking advantage of vulnerabilities in smaller platforms to reach specific targets, such as MOVEit, file transfer software; 3CX, a telephony solution; and PaperCut print management software. In June, for example, the Clop ransomware took advantage of a Zero Day vulnerability in MOVEit and compromised several government agencies in the United States, such as the Department of Energy, university systems in several states, and dozens of large organizations, such as British Airways, Siemens and Schneider Electric.
Malware Campaigns
The Trend Micro report highlights that the main targets of the malware campaigns were the government and industrial sectors, with around 145 thousand records each, followed by the areas of health (124,300), education (101,400) and technology (89,000). The United States, Japan and Italy were the countries with the highest number of malware campaign detections.

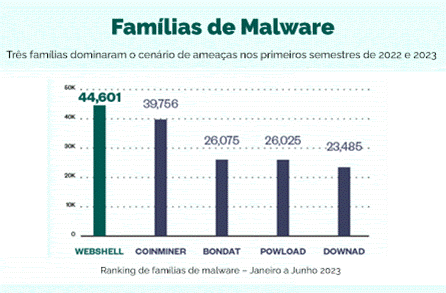
The three malware families that remain active are: Webshell – which has the highest number of cases, both in the first half of 2022 and 2023 –, CoinMiner, whose last reported action was the exploitation of Oracle WebLogic vulnerabilities; and the Bondat, first observed in 2013.
The report released by the Trend Micro research team on the threat landscape is based on the Trend Micro Smart Protection Network (SPN) solution, which analyzes data security infrastructure. In addition to SPN's sensors, the data collected also came from researchers at Trend Micro, the Zero Day Initiative (ZDI) team, the Threat Hunting teams, TippingPoint, Mobile Application Reputation Service (MARS), Smart Home Network (SHN ) and IoT Reputation services.
For more details on the report, go to ON HERE.













