New/old threat to rob bank customers
CLM and SentinelOne disclose modus operandi of the Neo_Net group, which has been stealing money and data from thousands of victims around the world

CLM, a Latin American value-added distributor focused on information security, data protection, cloud and data center infrastructure, releases the survey that won the first Malware Research Challenge, carried out by SentinelOne, specializing in AI-based (Artificial Intelligence) cybersecurity technologies ranging from prevention, detection, response and hunting to attacks, in partnership with vx-underground.
The challenge winner was Pol Thill, a researcher in the cybersecurity community, with an in-depth and meticulous study of Neo_Net, a cybercrime threat actor targeting thousands of customers using financial institution mobile apps. Thill even shows the use of a Smishing-as-a-Service, call of ankarex, which in addition to being used by the group is rented to other cybercriminals, further increasing the number of victims. Smishing is all Phishing that is distributed via SMS messages instead of emails. In Brazil, criminals even get 0800 call centers to give more credibility.
Francisco Camargo, CEO of CLM, which distributes SentinelOne solutions in Latin America, emphasizes the importance of this type of competition for significantly contributing to the understanding of the cybersecurity scenario in the world and the discovery of the modus operandi of cybercriminal groups.
“The research on Neo_Net was able to describe the step by step of this criminal operation and how it branches out. Yes, the cybercrime underworld has become a franchise, selling and renting off-the-shelf infrastructure. They have strategies, business gimmicks and advertisements to publicize their 'services' and make a profit”, he says.

Halloween offer with 15% of extra resources when reloading the account
Pol Thill found that Neo_Net's campaigns are done in several stages: phishing SMS messages targeted at bank customers, use of Smishing-as-a-Service, malicious links to fake pages that look very similar to those on bank apps, and create the illusion of authenticity, deceiving many account holders. The objective, in addition to stealing money, is to extract data.
Study
According to Thill's study, Neo_Net has been conducting an extensive e-Crime campaign targeting customers of major banks around the world from June 2021 to April 2023. The main focus of criminals are Spanish and Chilean banks, so much so that 30 of the 50 target financial institutions are based in Spain or Chile, including large banks such as Santander, BBVA and CaixaBank. Target institutions in other regions include Deutsche Bank, Crédit Agricole and ING. A complete list is in Appendix A at the end of the text.
Despite using relatively unsophisticated tools, Neo_Net achieved a high success rate by adapting its infrastructure to specific targets, which resulted in the theft of over €350,000 from victims' bank accounts and compromised Personally Identifiable Information (Personally Identifiable Information). PII) such as phone numbers, national identity numbers and the names of thousands of them.
Neo_Net established and leased extensive infrastructure including phishing panels, smishing software and Android trojans to various affiliates; sold compromised victim data and launched the ankarex, a successful offering of Smishing-as-a-Service, targeted at various countries around the world.
Technical detail
Below is the report detailing Neo_Net's campaigns and background that shed light on its operations over the years.
eCrime campaign against financial institutions
The campaign employs a multi-stage attack strategy, starting with targeted phishing SMS messages distributed across Spain and other countries, and using Neo_Net's proprietary service, Ankarex, its Smishing-as-a-Service platform.
These messages leveraged sender IDs (SIDs) to create an illusion of authenticity, mimicking reputable financial institutions to trick victims.
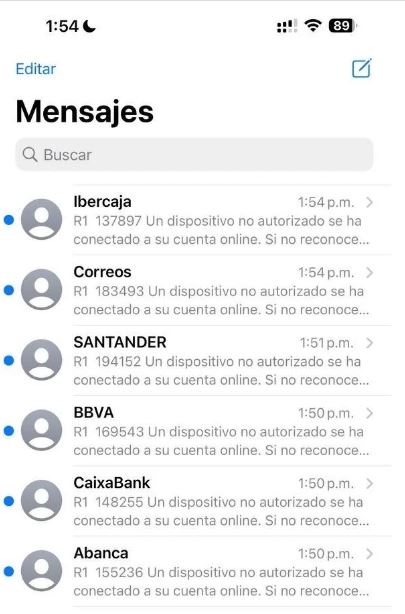
Demonstration of Ankarex SID functionality on Ankarex News Channel
SMS messages use various scare tactics, such as claiming that the victim's account was accessed from an unauthorized device or that their card limit was temporarily limited due to security concerns.
The messages also contain a hyperlink to a criminal's phishing page.
The phishing pages are meticulously configured using Neo_Net's panels, PRIV8, and implement several defensive measures, including blocking requests from users accessing from non-mobile devices and hiding the pages from bots and network scanners. These pages are designed to resemble genuine banking apps, complete with animations to create a convincing facade:
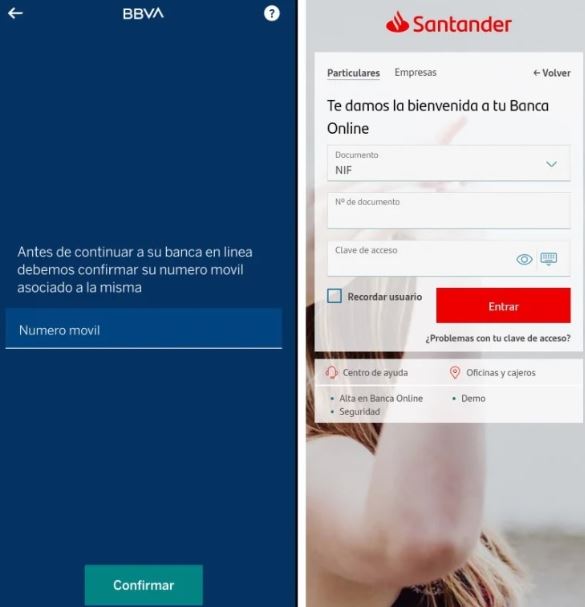
BBVA and Santander phishing pages
After submitting credentials, victims' information is illicitly exfiltrated into a Telegram chat via the Telegram Bot API, granting criminals unrestricted access to stolen data, including victims' IP addresses and user data.
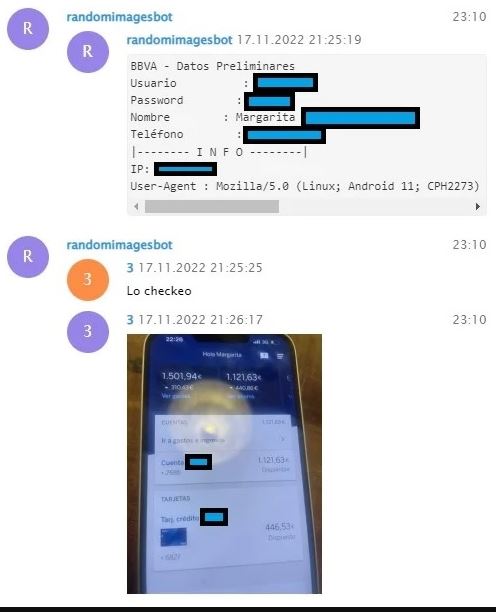
Neo_Net Affiliates discussing captured credentials and corresponding bank account
Later, attackers employed various techniques to bypass multi-factor authentication (MFA) mechanisms commonly used by banking applications. One such approach involves tricking victims into installing a supposed security app for their bank account on their Android devices.

Android app representing ING
However, this app does not serve any legitimate security purpose and only requests permissions to send and view SMS messages.
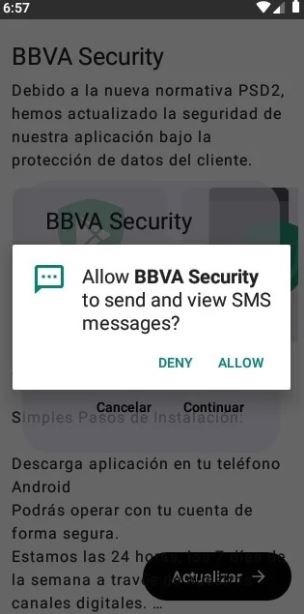
BBVA App – SMS permission request after victim clicks “Update” button
In reality, these Android trojans functioned as modified versions of the publicly available SMS spyware for Android known as SMS Eye. Some threat actors further obfuscated the trojan by using public wrappers to avoid detection by anti-malware solutions. These trojans secretly exfiltrate incoming SMS messages to an exclusive Telegram chat.
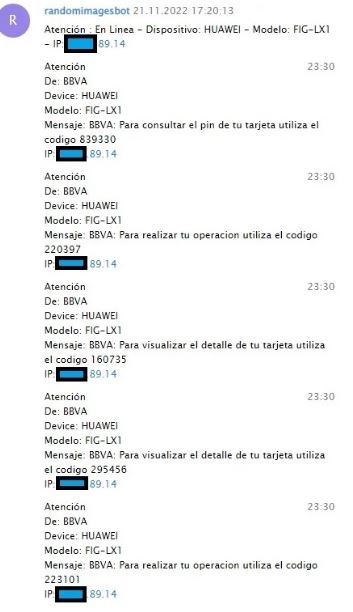
Telegram messages showing exfiltrated BBVA OTPs
The exfiltrated messages are then used to bypass MFA on target accounts by capturing one-time passwords (OTPs). Furthermore, criminals have also been observed making direct phone calls to victims, possibly to impersonate bank representatives and trick them into installing Android spyware or disclosing their OTPs.
The amount acquired illicitly from the victims during one year of operation totaled at least 350 thousand euros. However, the true value is likely to be significantly higher as older operations and transactions that do not involve SMS confirmation messages may not have been fully accounted for due to limited visibility.
Neo_Net
Neo_Net, the prominent actor responsible for the global cybercrime campaign, has been active in the cybersecurity scene since at least the beginning of 2021. They maintain a public profile on GitHub under the name “notsafety” and a Telegram account that showcases his work and identifies him as the founder of Ankarex, a Smishing-as-a-Service platform.
Neo_Net profile on Telegram
Through their contributions on Telegram, Neo_Net was linked to the forum “macosfera.com”, an IT forum in Spanish. Email addresses registered with the forum's domain were found in relation to several phishing panels created by Neo_Net, which targeted Spaniards and other institutions. These email addresses were used as usernames for the panels, suggesting that Neo_Net may have collaborated with individuals on this forum to set up its infrastructure. Phishing panels also clearly indicate Neo_Net as the creator with their signature at the top of php files.
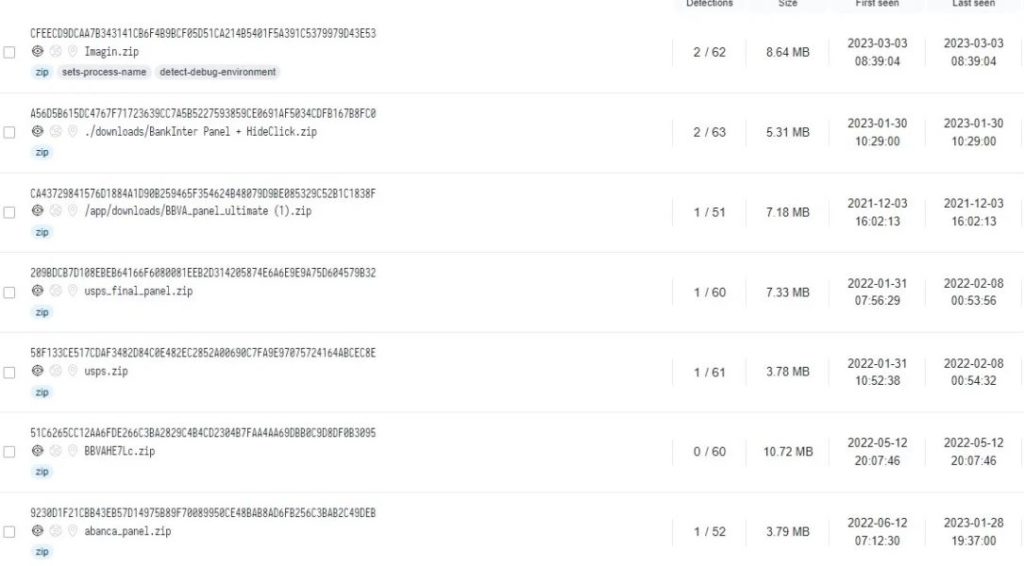
Phishing panels linking to macosfera[.]com (VirusTotal)
ankarex
The main creation of Neo_Net is the Ankarex Smishing-as-a-Service platform, which has been active since at least May 2022. The Ankarex News Channel on Telegram, which advertises the service, currently has 1700 subscribers and regularly publishes updates about the software , as well as limited offers and freebies.
The service will be accessed on ankarex[.]net and, once registered, the user can upload resources using cryptocurrency transfers and then launch their own Smishing campaigns by specifying the SMS content and target phone numbers. Ankarex currently targets nine countries, but has historically operated in other regions.
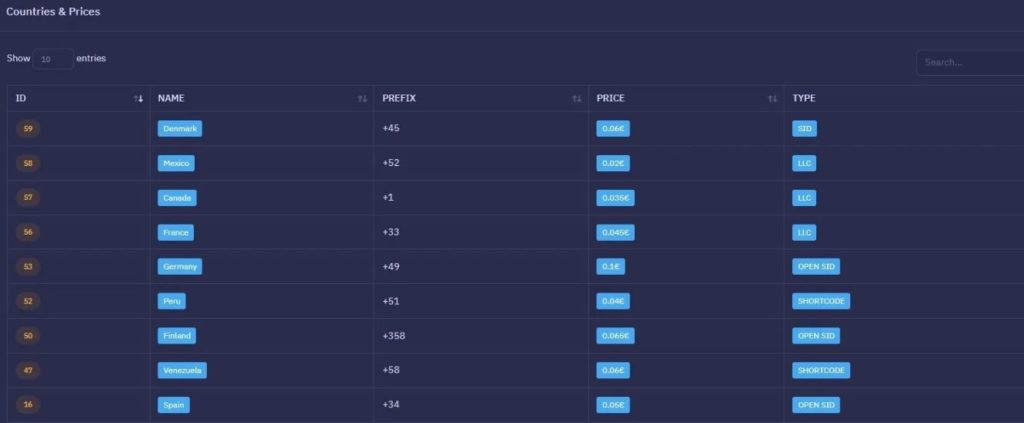
Ankarex price list and target countries
In addition to the Smishing service, Neo_Net also offers leads including victims' names, email addresses, IBANs and phone numbers for sale on the Ankarex Channel. He also announced his Android SMS spyware service to select members. Notably, every channel created to exfiltrate captured SMS messages has Neo_Net listed as the administrator, and several Android Trojan package names allude to their creator with names like com.neonet.app.reader. It is likely that Neo_Net has leased its infrastructure to affiliates, some of whom have been observed working with it on various unique campaigns, allowing them to independently conduct phishing and asset transfers.

Neo_Net demonstrating Ankarex on its own phone and displaying remarkable OPSEC throughout its campaigns
Over the course of its year-long operation, Neo_Net has been traced to several unique IP addresses, indicating that it currently resides in Mexico. Neo_Net operates primarily in Spanish speaking countries and communicates predominantly in Spanish with its affiliates. Communication on the Ankarex Channel is almost exclusively done in Spanish.
However, Neo_Net has also been observed collaborating with non-Spanish speakers, including another cybercriminal identified by Telegram as devilteam666. This particular operation involved the use of Google Ads targeting crypto wallet owners, and devilteam666 continues to offer malicious Google Ads services on its Telegram channel.
Appendix A: Target Financial Institutions
- Spain: Santander, BBVA, CaixaBank, Sabadell, ING España, Unicaja, Kutxabank, Bankinter, Abanca, Laboral Kutxa, Ibercaja, BancaMarch, CajaSur, OpenBank, Grupo Caja Rural, Cajalmendralejo, MoneyGo, Cecabank, Cetelem, Colonya, Self Bank, Banca Pueyo
- France: Crédit Agricole, Caisse d'Epargne, La Banque postale, Boursorama, Banque de Bretagne
- Greece: National Bank of Greece
- Germany: Sparkasse, Deutsche Bank, Commerzbank
- United Kingdom: Santander UK
- Austria: BAWAG PSK
- Netherlands:ING
- Poland: PKO Bank Polski
- Chile: BancoEstado, Scotiabank (Cencosud Scotiabank), Santander (officebanking), Banco Ripley, Banco de Chile, Banco Falabella, Banco de Crédito e Inversiones, Itaú CorpBanca
- Colombia: Bancolombia
- Venezuela: Bank of Venezuela
- Peru: BBVA Peru
- Ecuador: Banco Pichincha
- Panama: Zinli
- USA: Prosperity Bank, Greater Nevada Credit Union
- Australia: CommBank
Appendix B
Commitment indicators
| APK SHA1 Hashes | Main activity name | personified institution |
| de8929c1a0273d0ed0dc3fc55058e0cb19486b3c | com.neonet.app.reader.MainActivity | BBVA |
| b344fe1bbb477713016d41d996c0772a308a5146 | com.neonet.app.reader.MainActivity | Labor Kutxa |
| 8a099af61f1fa692f45538750d42aab640167fd2 | com.neonet.app.reader.MainActivity | post office |
| ab14161e243d478dac7a83086ed4839f8ad7ded8 | com.neonet.app.reader.MainActivity | BBVA |
| ded2655512de7d3468f63f9487e16a0bd17818ff | com.neonet.app.reader.MainActivity | CaixaBank |
| a5208de82def52b4019a6d3a8da9e14a13bc2c43 | com.neonet.app.reader.MainActivity | CaixaBank |
| 21112c1955d131fa6cab617a3d7265acfab783c2 | com.neonet.app.reader.MainActivity | openbank |
| 6ea53a65fe3a1551988c6134db808e622787e7f9 | com.neonet.app.reader.MainActivity | Unicaja |
| 62236a501e11d5fbfe411d841caf5f2253c150b8 | com.neonet.app.reader.MainActivity | BBVA |
| 7f0c3fdbfcdfc24c2da8aa3c52aa13f9b9cdda84 | com.neonet.app.reader.MainActivity | BBVA |
| f918a6ecba56df298ae635a6a0f008607b0420b9 | com.neonet.app.reader.MainActivity | Santander |
| ffbcdf915916595b96f627df410722cee5b83f13 | com.neonet.app.reader.MainActivity | BBVA |
| 7b4ab7b2ead7e004c0d93fe916af39c156e0bc61 | com.neonet.app.reader.MainActivity | CajaSur |
| 34d0faea99d94d3923d0b9e36ef9e0c48158e7a0 | com.neonet.app.reader.MainActivity | BBVA |
| e6c485551d4f209a0b7b1fa9aa78b7efb51be49b | com.neonet.app.reader.MainActivity | BBVA |
| 1df3ed2e2957efbd1d87aac0c25a3577318b8e2a | com.neonet.app.reader.MainActivity | BBVA |
| 6a907b8e5580a5067d9fb47ef21826f164f68f3f | com.neonet.app.reader.MainActivity | Caja Rural Group |
| 5d1c7ff3d16ec770cf23a4d82a91358b9142d21a | com.neonet.app.reader.MainActivity | Caja Rural Group |
| 86ad0123fa20b7c0efb6fe8afaa6a756a86c9836 | com.neonet.app.reader.MainActivity | Caja Rural Group |
| 14a36f18a45348ad9efe43b20d049f3345735163 | com.neonet.app.reader.MainActivity | Cajalmendralejo |
| b506503bb71f411bb34ec8124ed26ae27a4834b9 | com.neonet.app.reader.MainActivity | BBVA |
| afe84fa17373ec187781f72c330dfb7bb3a42483 | com.cannav.cuasimodo.jumper.activities | BBVA |
| 445468cd5c298f0393f19b92b802cfa0f76c32d4 | com.cannav.cuasimodo.jumper.activities | BBVA |
| 8491ff15ad27b90786585b06f81a3938d5a61b39 | com.cannav.cuasimodo.jumper.activities | BBVA |
| 2714e0744ad788142990696f856c5ffbc7173cf4 | com.cannav.cuasimodo.jumper.activities | BBVA |
| 1ce0afe5e09b14f8aee6715a768329660e95121e | com.cannav.cuasimodo.jumper.activities | BBVA |
| 96a3600055c63576be9f7dc97c5b25f1272edd2b | com.cannav.cuasimodo.jumper.activities | BBVA |
| 9954ae7d31ea65cd6b8cbdb396e7b99b0cf833f4 | com.cannav.cuasimodo.jumper.activities | BBVA |
| 07159f46a8adde95f541a123f2dda6c49035aad1 | com.cannav.cuasimodo.jumper.activities | BBVA |
| ab19a95ef3adcb83be76b95eb7e7c557812ad2f4 | com.cannav.cuasimodo.jumper.activities | BBVA |
| db8eeab4ab2e2e74a34c47ad297039485ff75f22 | com.cannav.cuasimodo.jumper.activities | BBVA |
| dbf0cec18caabeb11387f7e6d14df54c808e441d | com.cannav.cuasimodo.jumper.activities | BBVA |
| 69d38eed5dc89a7b54036cc7dcf7b96fd000eb92 | com.cannav.cuasimodo.jumper.activities | BBVA |
| c38107addc00e2a2f5dcb6ea0cbce40400c23b49 | com.cannav.cuasimodo.jumper.activities | BBVA |
| 279048e07c25fd75c4cef7c64d1ae741e178b35b | com.uklapon.mafin.chinpiling.activities | bankinter |
| ef8c5d639390d9ba138ad9c2057524ff6e1398de | BBVA | |
| e7c2d0c80125909d85913dfb941bdc373d677326 | ING | |
| 145bd67f94698cc5611484f46505b3dc825bd6cd | State Bank |
phishing domains
bbva.info-cliente[.]net
santander.esentregas[.]ga
bbva.esentregas[.]ga
correos.esentregas[.]ga
Appendix C: MITER ATT&CK tags
| ID | Technique | Explanation |
| T1406.002 | Obfuscated Files or Information: Software Packing | Some APK files are packed and drop the unpacked dex file once executed |
| T1633.001 | Virtualization/Sandbox Evasion: System Checks | Some APK files have been modified and initially check for common sandbox names before unpacking |
| T1426 | System Information Discovery | The Sms Eye trojan collects the brand and model of the infected phone |
| T1636.004 | Protected User Data: SMS Messages | The Sms Eye trojan collects incoming SMS messages |
| T1437.001 | Application Layer Protocol: Web Protocols | The Sms Eye trojan exfiltrates SMS messages over HTTPS |
| T1481.003 | Web Service: One-Way Communication | The Sms Eye trojan uses the Telegram Bot API to exfiltrate SMS messages |
| T1521.002 | Encrypted Channel: Asymmetric Cryptography | The C2 channel is encrypted by TLS |
| T1646 | Exfiltration Over C2 Channel | The SMS messages are exfiltrated over the C2 channel |













