Trend Micro study shows that small and medium-sized businesses in North America and Europe are preferred by top ransomware groups

An ever-evolving ecosystem, increasingly sophisticated and with new players and infiltration and extortion schemes. This is the world of cybercrime when it comes to ransomware gangs – which in 2022 promoted almost 16 million attacks on companies. Trend Micro researchers, a world leader in cybersecurity solutions, analyzed hacker activity and concluded that three families dominated the world stage: LockBit, BlackCat and royal, a dissident group from Conti, one of the most aggressive in recent years.
A close look at the leak sites of the groups of ransomware (those who publish attacks on companies that were successfully compromised but refused to pay the ransom) shows that organizations based in the United States were hardest hit by this type of attack, in the last quarter of 2022, representing 42% of the total victims. The scams also affected several European countries, such as the United Kingdom and Germany, in addition to Brazil.
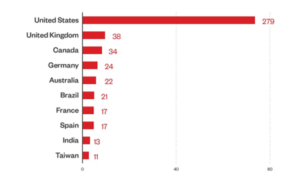
Top 10 countries affected by successful RaaS and extortion attacks in Q4 2022. Source: RaaS and extortion group leak sites and Trend Micro's OSINT (Open Source Intelligence) research.
LockBit was the most active Ransomware as a Service (RaaS) provider in the period, which reinforces the findings of reports released in the first, second and third quarters of 2022. BlackCat, on the other hand, has come up with new extortion tricks, including the impersonation of a victim's website in order to use it to publish stolen data on the web. The Royal group, on the other hand, combined old and new techniques to access their targets, suggesting an extensive knowledge of the ransomware scene.
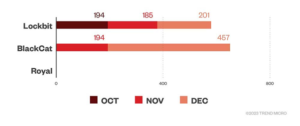
Number of LockBit, BlackCat, and Royal ransomware file detections, on machines, by month, in Q4 2022. Source: Trend Micro™ Smart Protection Network™.
lockbit
LockBit was the most prominent group in 2022, firmly holding the top spot from January to December. It took out more than a third of organizations attacked in the first (35.8%), second (34.9%) and third (32.9%) quarters, although its share dropped significantly in the last quarter of the year (22.3%). Of the Q4 attacks, 11.7% were by BlackCat and 10.7% attributed to Royal.
Since its discovery in September 2019, LockBit has built a track record of frequently updating its malware resources and implementing affiliate expansion programs to solidify its position in the RaaS field. In addition to using double extortion skillfully, LockBit has also been launching innovative initiatives.
According to data from the leak site, more than half of its victims were small organizations (with a maximum of 200 employees), representing 51.7% of investees in the fourth quarter. Medium-sized companies (with 201 to 1,000 employees) accounted for 21.7%, while large companies (with more than 1,000 employees) accounted for 15.6%. The finance, IT and healthcare sectors were the main targets in the period and more than a third of victims are based in North America, with 44%.
black cat
Before saying goodbye to the year, BlackCat compromised an organization in the financial services industry using a creative extortion tactic to punish victims for not meeting ransom demands. First, he published all the data obtained on the gang's own website (Tor) and then leaked stolen files on a replica website of the victim, using a domain name typosquatted. As websites published on the dark web have limited visibility, sharing stolen information on the internet puts more pressure on the victim as it is accessible to the general public.
BlackCat operators also abused a Telegram account to promote their new RaaS offering: a prepackaged Log4J Auto Exploiter. BlackCat operators claim that the tool can be used to spread BlackCat malware laterally within a network.
royal
Several attacks by the Royal group were seen in 2022 mainly against organizations in the US and Brazil. The use of phishing callback mode to trick victims into installing malware on remote desktop allows contamination of machines with minimal effort. Meanwhile, the ransomware group's burst encryption tactics also speed up the encryption of victims' files.
In its first campaigns, Royal deployed the BlackCat encryptor. It then switched to its own called Zeon, which leaves ransom messages similar to Conti's. Later he customized the notes with his new encryptor. Small businesses accounted for 51.9% of Royal's victims in Q4, while mid-sized organizations gained a share of 26.8%. Large companies accounted for 11.3% in this period.
In December, the US Department of Health issued a warning to healthcare organizations warning of threats from the Royal ransomware. One report mentioned that ransom demands ranged from US$ 250 thousand to over US$ 2 million. Royal is supposedly a private group with no affiliates. Therefore, it cannot be classified as a RaaS provider.
The study on top ransomware families is based on data from extortion groups' RaaS leak sites in the Open Source Intelligence Survey (OSINT / Open Source Intelligence) from Trend Micro and information from the Trend Micro™ Smart Protection Network™ platform.













