Vulnerabilities in macOS endpoints, low detection rate, weak passwords, difficulty in defending against ransomware are some findings from the Picus Blue Report 2024
40% of more than 136 million environments presented vulnerabilities that could give access to the domain administrator and, consequently, total control of the network by cybercriminals. This access allows attackers to control user accounts, security settings, and general network management. The information is from Picus Blue Report 2024, published by CLM, a Latin American value-added distributor focused on information security, data protection, cloud and infrastructure for data centers, the company's main partner in Latin America.
The president of CLM, Francisco Camargo, explains that access to the domain administrator needs to be one of the main concerns of security teams because this breach can lead hackers to have full control of a corporation's IT infrastructure. “The danger is too great! The domain administrator access level allows attackers to control user accounts, security settings and the entire network”, he points out.
The annual study Picus Blue Report 2024 was conducted by Picus Labs, a research unit at Picus Security, which analyzed more than 136 million attack simulations to evaluate the effectiveness of cybersecurity solutions used by companies. The report highlights the need for this validation of solutions and continuous fine-tuning, as the only way to discover high-risk attack paths.
Effectiveness of cybersecurity solutions in the real world
Picus Security has observed significant variability between the performance of cybersecurity products in controlled environments versus real-world settings. Solutions that score 100% in assessments such as MITER ATT&CK can, unfortunately, exhibit significant variability in effectiveness once deployed in diverse operational environments.
Easy-to-crack passwords
In addition to the constant evolution of cybercrime, hacktivism, and the use of AI for illicit purposes, cybersecurity continues to face common, recurring problems, such as weak passwords. “It is surprising to see that 25% of environments still use passwords that can be cracked using common words”, comments Camargo.
BlackByte was the most successful ransomware group
When it comes to ransomware, the findings are equally concerning. BlackByte was the most difficult ransomware variant to defend against, with only 17% success rate. BabLock and Hive followed closely, with prevention rates of 20% and 30% respectively.
“It is crucial to adopt stronger and more effective cybersecurity measures, with proactive approaches such as breach and attack simulation (BAS). Cybersecurity needs to be seen as a continuous battle that requires attention, innovation and adaptation, and it is essential to understand the risk to improve defenses, correct critical vulnerabilities and improve the security posture”, warns the executive.
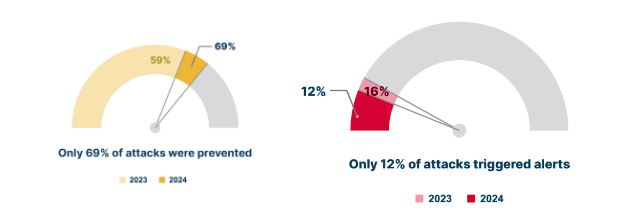
Prevention up, detection down: a cyber defense paradox
Although there has been a notable improvement in prevention effectiveness, which increased from 59% in 2023 to 69% in 2024, detection effectiveness has left something to be desired. O alert score fell from 16% to 12% in the same period. This reduction suggests that increased logging has not translated into better visibility and faster threat detection. The disparity points to the need for organizations to prioritize optimization across their entire detection engineering pipeline.
Challenges of Detection Rules in SIEM Systems
Most of the issues that Picus identified in SIEM system detection rules were related to log collection (38%) and performance (33%). Inadequate log source consolidation affected 23% of cases, while unavailable (10%) and broken (5%) log sources further deepened detection challenges.
Vulnerabilities in macOS endpoints
O Picus Blue Report 2024 showed that macOS endpoints were much more likely to be misconfigured or operate correctly without Endpoint Detection and Response (EDR) tools. As a result, macOS endpoints only prevented 23% of the simulated attacks, compared to 62% and 65% blocked by Windows and Linux. For Picus Security, this finding suggests that security teams are not allocating adequate resources to protect these systems.













