 *Per Franzvitor Fiorim
*Per Franzvitor Fiorim
The “as-a-Service” model has been gaining adaptations around the world and it is not new that hackers have embarked on this wave, selling access to tools, instructions and lists of vulnerable targets. This is a trend that could shape the future of the vulnerability exploitation market, even more with the creation of platforms for cybercriminals offering advantages such as easy and remote connection to corporate networks via RDP (Remote Desktop Protocol).
The study The Rise and Imminent Fall of the N-Day Exploitation Market in the Cybercriminal Underground reveals that the “as-a-Service” model allows hackers to charge higher prices than N-Day exploits. The values charged generally start at more than US$ 1 thousand. For example, a seller offered access through Remote Code Execution (RCE) to a bank in France for US$ 1,200 and to a bank in Poland for US$ 1,500. To get an idea of how profitable it is, in some English forums Microsoft Word and Excel exploits are offered for just US$ 35.
In this context, we observe two types of “as-a-Service” sellers: the less experienced and the more professional. Less experienced people usually don't devote all their time to the sport and need to rely on luck to find explorations that work. Professional sellers, on the other hand, have a wide range of options for sale and even have a portfolio with the main offers traded on the market.
Vulnerability exploits that have been patched for years are cheap on the deep web and continue to make victims. Variants of the WannaCry ransomware, for example, which emerged in 2017, are still prevalent today. Trend Micro's annual cybersecurity report shows that WannaCry was the most detected malware family in 2020. And according to Shodan, in a search conducted last June, there are still more than 650,000 devices vulnerable to this family of ransomware.
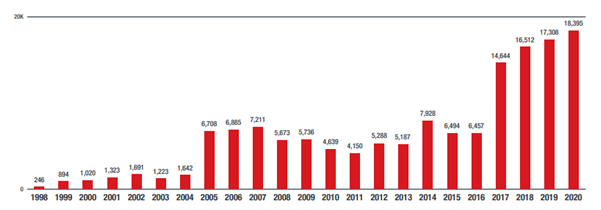
During our research, we saw the price of a holding continually drop over time until it eventually dropped to zero. This made exploitation accessible to more cybercriminals. Paradoxically, the longer it has elapsed since a patch is released for a vulnerability, the greater the attack surface, as pricing allows the most malicious attackers to incorporate vulnerability exploitation into their business models.
But if a vulnerability is already patched, why is it still profitable and claiming victims around the world? The observation is that most companies are not prepared to deal with this danger. It is necessary to create a security culture, understand that old vulnerabilities pose risks and need to be remedied. Virtual patching is a way for organizations to buy time for security teams to implement necessary updates.
When analyzing the potential risk that vulnerabilities pose, organizations should consider more than just the scores of gravity; they must also look at what is being exploited in the cybercrime underworld. The longevity of a valuable farm is longer than most people think. This information is vital for anyone managing an organization's cyber security. By addressing yesterday's popular vulnerability you can often be eliminating today's most critical risk.
*Franzvitor Fiorim is Technical Director at Trend Micro Brasil
Notice: The opinion presented in this article is the responsibility of its author and not of ABES - Brazilian Association of Software Companies













