 * By Francisco Camargo
* By Francisco Camargo
Companies are literally in the clouds. To give the dimension of this, cloud computing already represents, on average, 42% of processing in companies in Brazil, according to the Annual Survey of the Center for Applied Information Technology of the Getúlio Vargas Foundation (FGVcia). But as organizations move their business applications to various cloud environments, many challenges arise, especially for data protection, which the landscape is bleak with cyber plagues relentlessly plaguing every enterprise.
Cloud adoption, coupled with transformations in corporate ways of doing things, especially hybrid work, have rendered many data protection technologies obsolete. This is the case of traditional VPNs (Virtual Private Network), which were outdated in the face of the fierce cat and mouse dispute – cybercrime and companies victims of attacks (in that order) – for not keeping up with the true disruption of criminals.
To replace them, companies specializing in cybersecurity have developed Private Access solutions, based on ZTNA (Zero Trust Network Access) technology, an evolution of VPNs. Created within the principle of Zero Trust and the necessary scope to manage access anytime anywhere any device, ZTNA is a structure for security and access to workloads and multicloud applications, with controls and protection policies, based on context.
In virtual private networks this is not the case. Therefore, the biggest problem with the VPN is to allow the user, at home, to access the entire company network, all the information contained therein, using a login and password. Even having some limitation, the door is always open. This lack of restriction and granularity can compromise security. So much so that, according to the Thales Data Threat Report, 46% of respondents said they had suffered a data breach in the last 12 months.
Instead of having access to the entire company network, with ZTNA, the user only enters specific applications that he needs to use at that moment. And every time he accesses the application, validation needs to be done again, considering all controls at each access. The path is not open. Access to apps is denied by default. Policies are granular, adaptive, and context-aware, ensuring secure, seamless Zero Trust access to private applications hosted in clouds and corporate data centers.
“Context awareness” can be a combination of the user's identity, location, time, type of service, and device security posture.
Not wanting to massacre VPNs, but already massacring. One of its main obstacles is not being able to monitor each connecting device to protect access to the application and avoid data exfiltration. Another difficulty is slowness. VPNs were not designed to support remote and distributed work. Backhaul, which takes each user's connection through centralized VPN hubs, has bandwidth and performance issues, which affect the experience.
In ZTNAs, on the contrary, users can connect directly to the application, which makes access to corporate resources, hosted in IaaS environments or private data centers, fast and secure.
But what are the real benefits of ZTNA?
Now, one of the essential resources for the protection of accesses is the micro-segmentation of networks. With it, enterprises can create software-defined perimeters and literally divide the corporate network into multiple micro-segments, preventing lateral movement of attackers and reducing the attack surface in the event of a breach.
It also makes apps invisible on the web, creating a virtual darknet that prevents apps from being discovered on the public internet. In this way, ZTNA protects against exposure of data that remain on the internet, malware and DDoS attacks.
If the company has legacy applications hosted in private data centers, ZTNA extends all its capabilities to them, greatly facilitating secure connectivity. And it keeps remote access, whether for private applications or SaaS, fast and uninterrupted directly in the cloud, which elevates the user experience.
VPN vs ZTNA
The fundamental difference between VPN and ZTNA is access. The former protects access at the network level and ZTNA at the application level. As mentioned, VPNs allow full access to the private network for any user with a valid login and password, overexposing sensitive corporate resources to compromised accounts and insider threats. Hackers who gain access to the entire network can freely move through internal systems undetected.
ZTNA restricts user access to specific applications strictly on a “need to know” or to use basis, limiting data exposure and lateral movement of threats in the event of a cyberattack. There is control, least privileges, and all connection requests are checked before granting access to internal resources, essential thresholds to prevent violations.
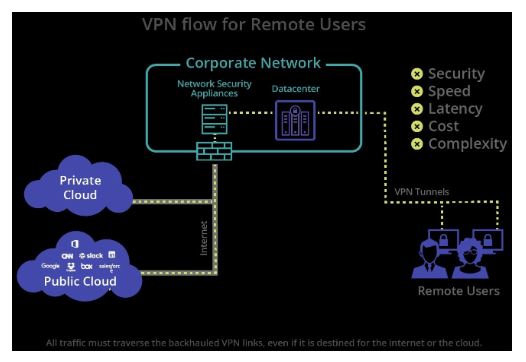
VPNs also lack application-level controls and visibility into user actions when inside the private network. ZTNAs record all actions, providing deeper visibility and monitoring of each user's behavior and risks. This allows you to enforce both information-based and data-centric controls to protect sensitive content within applications.
Another point unfavorable to VPNs is that their connections do not analyze the risks of the devices of those who enter the network. A compromised or malware-infected device can easily connect to the server and gain access to internal resources. ZTNAs continually assess connected devices, validate security posture, and allow tailored access to resources based on the device trust required at that time. If a risk is detected, the connection is terminated immediately.

At its heart, security is a data protection issue, especially in a cloud-first world. You can no longer use old approaches to protect information.
*Francisco Camargo is founder and CEO of CLM
Notice: The opinion presented in this article is the responsibility of its author and not of ABES - Brazilian Association of Software Companies













