Study reveals an increase of almost 350% in the detection of email malware in the last year, indicating a trend towards the use of malicious attachments in attacks
Trend Micro's annual balance sheet, global leader in cybersecurity, raises an alert for the need for companies to adapt their cybersecurity arsenal. In 2023, almost 161 billion attacks were blocked, 10% more than in 2022 and almost double the number of threats recorded five years ago, which was approximately 82 million.
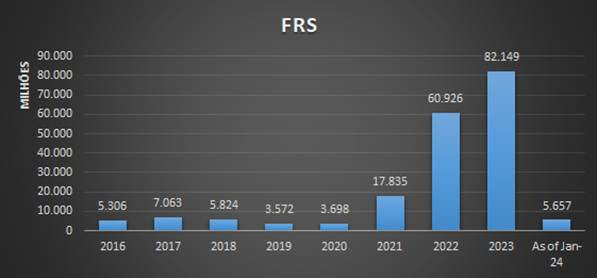
Attacks carried out via contaminated files, according to Trend Micro report
Analyzing the types of attacks carried out in 2023, it is noted that attacks via contaminated files showed the greatest growth (35%, as shown in the graph above), a strong indicator that attackers are selecting their victims more carefully. “Instead of sending a huge number of emails or websites with malicious links, cyber criminals adopted the strategy of hitting fewer targets, but with greater potential for financial gain. They do this by bypassing layers of early detection such as network and email filters, which explains the increase in malicious files in endpoints”, details Cesar Candido, general director of Trend Micro in Brazil.
Other trends noted in the report include:
- Variety and sophistication in Advanced Persistent Threat (APT) attacks Advanced Persistent Threat), especially in defense evasion tactics;
- Email malware detections increased by almost 350%, while malicious URL and phishing detections fell by 27%, reemphasizing the trend of using malicious attachments in attacks;
- 16% growth in Business Email Compromise (BEC) detections, also known as CEO fraud;
- 14% drop in ransomware detections; however, the increase in file-based threat reporting may indicate that criminals are getting better at avoiding primary detection in LOLBins/LOLBas (Living-off-the-Land Binaries and Scripts, which are native tools), BYOVD (from English, 'Bring Your Own Device'), Zero Day explorations and AV (audio and video) solutions;
- Increase in remote and intermittent encryption, EDR (Endpoint Response) bypass using unmonitored virtual machines (VMs), and multi-ransomware attacks, in which victims are hit more than once. Attackers recognized EDR as an excellent defense, but now they are able to apply tacticsbypass' to bypass technology;
- Thailand and the US were the most attacked by ransomware in 2023, with the banking sector being the main target of cybercrime;
- MITER ATT&CK's main detections were defense evasion, Command & Control, Initial Access, persistence and impact;
- Access to risky cloud applications was the top event detected by Trend Micro's attack surface risk management service, recording nearly 83 billion attempts;
- Trend Micro's Zero Day Initiative discovered and disclosed 1,914 Zero Day threats, an increase of 12% from the previous year. These included 111 Adobe Acrobat and Reader bugs. Adobe was most vulnerable software and PDF was the number one spam attachment type;
- Windows applications reached the top 3 in the ranking of exploited vulnerabilities that required virtual patches;
- Mimikatz (used in data collection) and Cobalt Strike (applied in Command & Control) remain the preferred cybercrime tools.
“We are blocking more threats than ever before and adversaries are increasingly showing greater variety and sophistication in their attacks, especially in defensive evasion. Our report highlights the need for proactive risk management across the entire attack surface, to understand adversaries’ strategies and act effectively”, recommends Jon Clay, Vice President of Threat Intelligence at Trend Micro.
Trend also advises that companies:
- Work with trusted security providers that take a comprehensive approach to cybersecurity, ensuring not only the protection of the environment, but also continuous monitoring for new vulnerabilities;
- Prioritize SOC efficiency by carefully monitoring cloud applications as they become more integrated into daily operations;
- Make sure all the latest patches/updates are applied to operating systems and apps;
- Utilize comprehensive security protocols to protect against vulnerabilities, enforce configuration settings, control application access, and enhance account and device security. Aim to detect ransomware attacks as early as possible, moving defenses through the initial access, lateral movement or data exfiltration stages.













