
Threat uses legitimate services with messages that intimidate victims
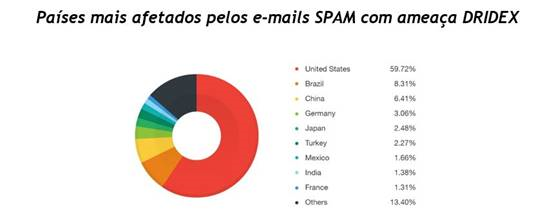
After apparent inactivity of Dridex – malware threat to online banking, during the beginning of this year, Trend Micro, a company specializing in the defense of digital threats and security in the era of the cloud, observed a sudden increase in a spam email campaign that mainly affected users in the United States, Brazil, China, Germany and Japan.
There are significant differences of this particular campaign from those previously applied. Instead of the usual fake invoices or notifications used as bait, Dridex plays on people's fear of having their accounts compromised. In addition to changing email subjects and macro usage, the scam uses the certutil, a Microsoft program that configures certificate services, backs up and restores certificate authority components to pass off the threat as a legitimate certificate. These two elements combined (use of macros and Certutil) can increase the prevalence of Dridex and pose challenges for detection.
Profiting from fear
Trend Micro analyzed an email message with the subject line, Committed Account and contains details of the alleged access attempt, including the IP address to make it appear legitimate. However, a loophole was found. The message lacks any information about what type of account (email, bank, social media accounts, etc.) is compromised. This type of notification typically mentions the type of account a remote user is trying to access.
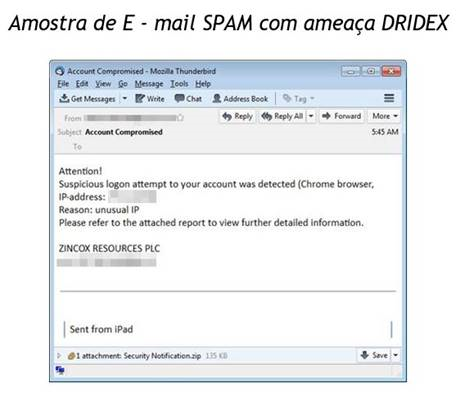
Based on research by Trend Micro, spam executed with Dridex is similar to locky ransomware using identical macros and email templates.
Leveraging Certutil
Regarding ransomware-related spam, it is a mistake to imagine that Dridex has lost its visibility in the threat landscape. With its new tactics, such as the use of Certutil and Personal Information Exchange (.PFX) files, a type of file used by certificate software that stores public and private keys, Dridex could regain its place again as the top online banking threat.
Since the file is downloaded in PFX format, it avoids Dridex detection and the use of macros allows similar occurrences to go unnoticed by sandbox technologies. This is a clear indication that Dridex is leveling off to remain the prevalent online banking threat.
What can users and organizations do?
Despite the prevalence of the threat, users and organizations can take some simple preventive measures such as not opening attachments and not enabling macros when receiving emails from unknown sources. Trend Micro advises that when you receive emails about compromised accounts, first check and verify the source.
Companies can also create policies that block email with attachments from unknown sources. It is also recommended that organizations educate their employees about this type of threat. Trend Micro endpoint solutions such as Trend Micro Security, Smart Protection Suitesit's the Worry Free™ Business Security can protect users and SMBs from this threat by detecting malicious files and spam email messages, as well as blocking all related malicious URLs.
O Trend Micro Deep Discovery, which has an email inspection layer, can protect companies by detecting malicious URLs and attachments. As such, it can prevent systems from getting infected with Dridex.













