* By Roberto Gallo
Hacker attacks have become increasingly common nowadays, not only due to the digitization of companies, but also due to the increase in users on the network as a result of the pandemic. Attacks like Spyware, Trojans, Rootkits, Worms and the notorious Phishing are carried out daily by malicious hackers and generally have the same objective: the theft of confidential and private information from both ordinary and specific users, in addition to websites and applications. Check out some of the most popular types of attacks below:
• Spyware: Collects information from the victim's browsing history;
• Trojans: Allusion to the Trojan horse built by the Greeks, attracts the victim by offering a bait, but hides a malicious action;
• Rootkit: Ensures administrative access to the attacker, enabling any action to be performed remotely;
• Worms: They replicate throughout the network, executing several different attacks and infecting as many machines as possible;
• Phishing: It seeks to deceive a victim with the intention of obtaining their personal information, such as passwords, credit card details and other documents.
According to the Anti-Phishing Working Group, Brazil had a 232% increase in security incidents related to phishing¹ in 2019, with its peak in November, caused mainly by two factors: the end-of-year shopping period, also associated with Black Friday, and year-end income increases, such as the thirteenth, for example.
Phishing emails often catch the victim's attention through specific and worrying subjects, along with a convincing email address, such as "empresa_suport@gmail.com", for example. The technique provides credibility to the subject, in addition to having a format similar or even identical to that of the personified company, inducing the user to trust the authenticity of the document.
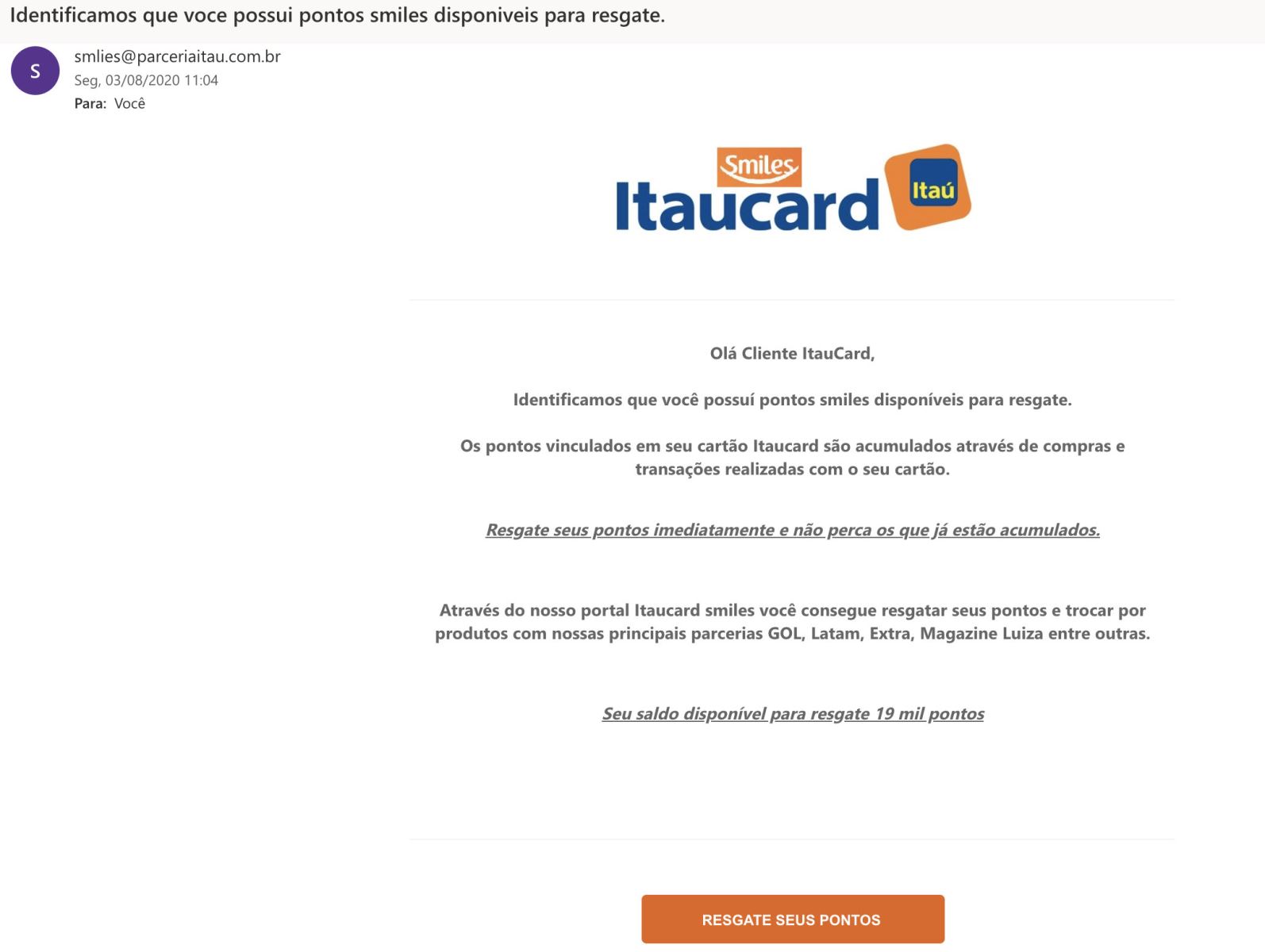
This type of attack happens due to the ease of execution, with no prerequisites or specific target, which allows scammers with little preparation to mount attacks. Phishing, on the other hand, generally affects more people with low education and low experience with technology, in particular, the elderly. However, these attacks have become increasingly sophisticated, and, consequently, more dangerous and difficult to identify. However, there are some points that, when taken into account, will help you to protect yourself against this type of attack.
Good customs can free you from a lot of trouble when it comes to accessing the internet. Look for: (i) changing your privacy settings to be more restrictive, (ii) not accessing applications that require authentication on a public network, (iii) keeping the browser up to date, and (iv) remembering to use two-factor authentication on social networks and in the application to access your credit card. E-mails that arouse curiosity or ask for personal information, such as credit card details, should be blocked and deleted. No financial institution asks for customer information by email. You should also be wary of login pages hosted on unknown domains, in addition to miraculous promotions that offer a price well below the market.
¹Source: http://docs.apwg.org/reports/apwg_trends_report_q4_2019.pdf
* Roberto Gallo is an Advisor to ABES - ABES - Brazilian Association of Software Companies, founding CEO of Kryptus, President of ABIMDE - Brazilian Association of Defense and Security Materials Industries and Director of the Federation of Industries of the State of São Paulo - FIESP.













